Top 6 Security Threats Targeting Healthcare Businesses
As of 2020, healthcare businesses faced a 55.1% increase in cyberattacks compared to the previous year, which exposed personal data from the accounts of both patients and the facility. Despite the benefits of modern systems, healthcare businesses still face difficulty in keeping up with security measures because of many factors, such as the amount of data present in their networks.
In this post, we’ll discuss why cybersecurity should be a business priority for healthcare organizations, which cyber threats are most common in the healthcare industry, and how you can protect your business from the costly repercussions of a cyberattack.
Cyberattacks in the Healthcare Sector
The healthcare sector faces several cybersecurity breaches every year, which cost millions of dollars in losses. In the U.S., healthcare facilities in California faced the most damage with 49 total hacking incidents in 2020 alone.
Forbes also reports that during these incidents, hackers were able to expose full names, addresses, contact details, and insurance information.
Relying on an outsourcing partner to protect your data is essential if you want operations to run smoothly. But before you can do this, you must first understand all of the possible security threats you could be faced with in the future. To learn more about the threats that healthcare businesses face, take a look at the infographics below.
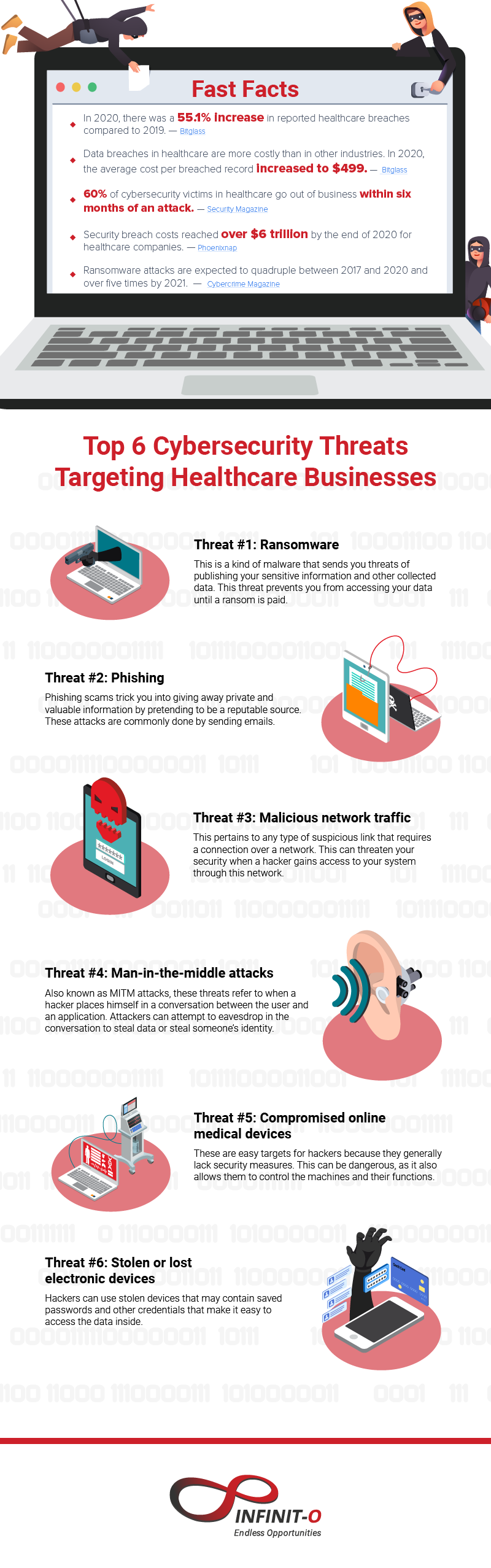
Top 6 Cybersecurity Threats Targeting Healthcare Businesses
There are several types of security threats that you can face in the future. Here are just a few of them.
Threat #1: Ransomware
Ransomware allows hackers to access your data and lock you out of your accounts until a ransom is paid. When this happens, you and other hospital staff cannot gain access to important data saved on your system. Simultaneously, hackers can also expose sensitive information and release them to the public.
Outsourcing your cybersecurity will allow you to upgrade your systems and avoid suspicious malware from being installed.
Threat #2: Phishing
Phishing occurs when you reply to a fraudulent email that tricks you into taking urgent action. Hackers use this tactic to steal sensitive information such as credit card details, passwords, and many more. Additionally, you can be attacked when you open suspicious email attachments, such as a document that requires you to open another program.
With a reliable outsourcing team on your side, suspicious emails and files can be double-checked for you to help you avoid accidental clicks that could harm your data.
Threat #3: Malicious network traffic
This refers to any type of connection made through clicking a link or file over a certain network. Malicious traffic allows hackers to make an impact on your security by compromising your computer and gaining access to all the data within it. These attacks can be done through unauthorized access and Distributed Denial of Service (DDoS) attacks.
Security threats like this can be handled by having a dedicated team improve and secure your networks. Limit access points and the use of public networks when going through sensitive data.
Threat #4: Man-in-the-middle attacks
Hackers commonly use this tactic to steal information such as passwords, account details, and credit card numbers. Most attacks typically occur on e-commerce websites or other platforms that require a login to access payment methods. In some cases, hackers also use this information to pretend to be someone else and steal your digital assets.
An outsourced partner can help you prevent these attacks by strengthening your website security, outgoing and incoming calls, and more. They can also help you secure private accounts on these websites and prevent tampering.
Threat #5: Compromised online medical devices
These devices are used to export information to other external sources to control how medical machines function. When breached, the data within could be manipulated to create complications and other issues that can harm patients in the process.
When you outsource your healthcare security with a reliable group, you can make these devices more secure by connecting them to a cloud-connected database. These storage systems can hold a significant amount of information and can prevent unwanted manipulation of connected devices.
Threat #6: Stolen or lost electronic devices
Devices that are used by healthcare employees can be stolen and used by hackers to access sensitive information. Once they have access to these accounts, it can be hard to detect a breach.
Partnering with a designated team to handle tools and other devices can help prevent theft and misuse.
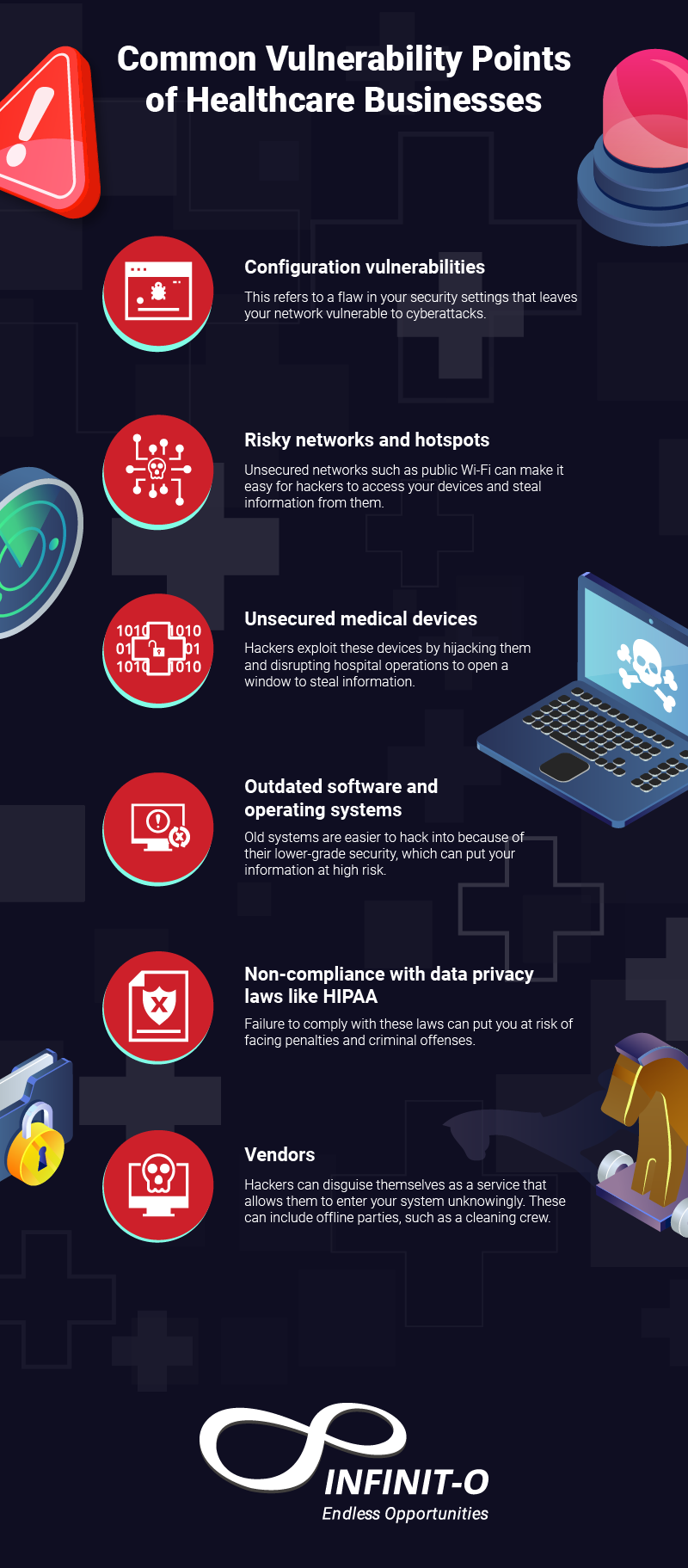
Common Vulnerability Points of Healthcare Businesses
Most healthcare businesses tend to face the same types of security threats. Here are some of the most common issues that can lead to cybersecurity breaches.
1. Configuration vulnerabilities
Hackers can access your network at any given time if you leave it with an unsecured access point. Connections can be made through any type of network that is linked to your systems such as a wireless network or a connected port.
2. Risky networks and hotspots
Unsecured networks such as public Wi-Fi and hotspots can reveal your IP address and other important information that cybercriminals need to access your account. These connections are also easy to hack into, which can leave your system vulnerable to attacks.
3. Unsecured medical devices
Most medical equipment doesn’t come with a built-in security system, which can make it easy for hackers to manipulate and control it. Ensure that these devices are out of reach in common corners of the facility and closely monitored by the right personnel.
4. Outdated software and operating systems
Using outdated systems can make you unable to keep up with heavier security measures while making it easy for hackers to break into. System errors and similar problems also become more common when using these tools.
5. Non-compliance with data privacy laws like HIPAA
If you fail to comply with privacy laws, you risk facing serious federal consequences and exposing your teams and other individuals to damages. There are also criminal fines and penalties that you must pay because of this.
6. Vendors
Most healthcare facilities hire third-party crews to take care of other tasks such as cafeteria work, cleaning, etc. This can be a vulnerability if proper background checks aren’t practiced such that hackers can disguise themselves and access your system without notice.
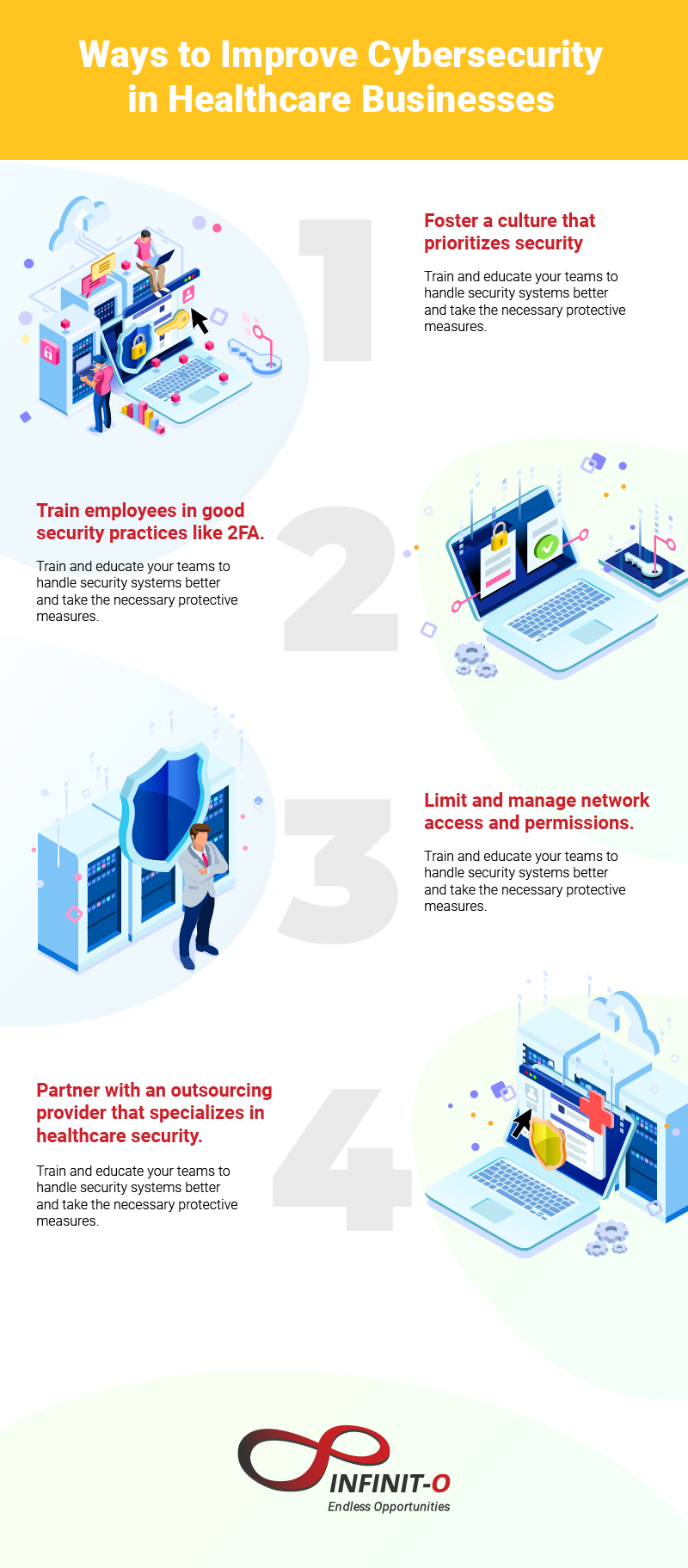
Ways to Improve Cybersecurity in Healthcare Businesses
Upgrading your cybersecurity system is the first step to protecting your sensitive data. Here are some methods you can apply for better security.
1. Foster a culture that prioritizes security.
Create an environment where security is taken as a priority and enable constant security checks on important access points. You can develop this culture by continuously practicing these measures and reminding teams to do the same.
2. Train employees in good security practices like two-factor authentication (2FA).
Always ensure that your employees are aware of proper security measures when handling accounts and connecting to sensitive networks. 2FA adds another layer of security since anyone attempting to access your data has to verify their identity and authority to be granted access.
3. Limit and manage network access and permissions.
Create a system that allows a limited amount of logins at a single point. This will allow you to easily track down activities and from which ports they have connected.
4. Partner with an outsourcing provider that specializes in healthcare security.
Look for a team of experts that specializes in healthcare security, such as Infinit-O. By partnering with our outsourcing team, you can better improve your security for a fraction of the cost.
Safety First
Healthcare businesses often don’t invest in the right security measures to protect their employees and patients because they often come with steep prices. Luckily, with a reliable outsourced healthcare security service, this issue can be handled by a team of experts that provide top-quality work at cost-effective rates.
Partner with Infinit-O today and gain a specialized team dedicated to keeping your data secure against possible threats while meeting your security needs. We are ISO 27001 and 9001 certified, GDPR, HIPAA, and DPA20212-compliant. Save as much as 70% on operational costs and relieve your worries with our 71 Net Promoter Score.
Start small. Exceed expectations. Think infinitely. Think Infinit-O.







This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.